Next-Gen Threat Detection, Driven by AI.
Vines Sees What Hackers Hide. Unmask Hidden Threats with AI Precision.

Powered by Artificial Intelligence
Harness next-gen AI to analyze complex data, identify vulnerabilities, and prioritize risks—delivering faster, smarter protection.

Real-Time Threat Detection
Continuous monitoring with advanced ML detects and responds to attacks the instant they happen—always-on threat intelligence.

Rocheston Aina Integrated
Aina, your AI security copilot, guides remediation step-by-step—making fixes simple, clear, and effective.

Integrate with Jira and Slack
Pipe findings straight into your workflow—auto-create Jira issues, push alerts to Slack channels, and track fixes from detection to closure without context-switching.

CI/CD Pipelines
Shift left with DevSecOps—run Vines in CI/CD to block risky builds, gate merges on severity policies, and emit audit-ready artifacts that keep releases fast and secure.

API Endpoints
Automate at scale with REST APIs and webhooks—pull results, trigger rescans, sync dashboards, and integrate Vines data across your tooling with stable, versioned endpoints.
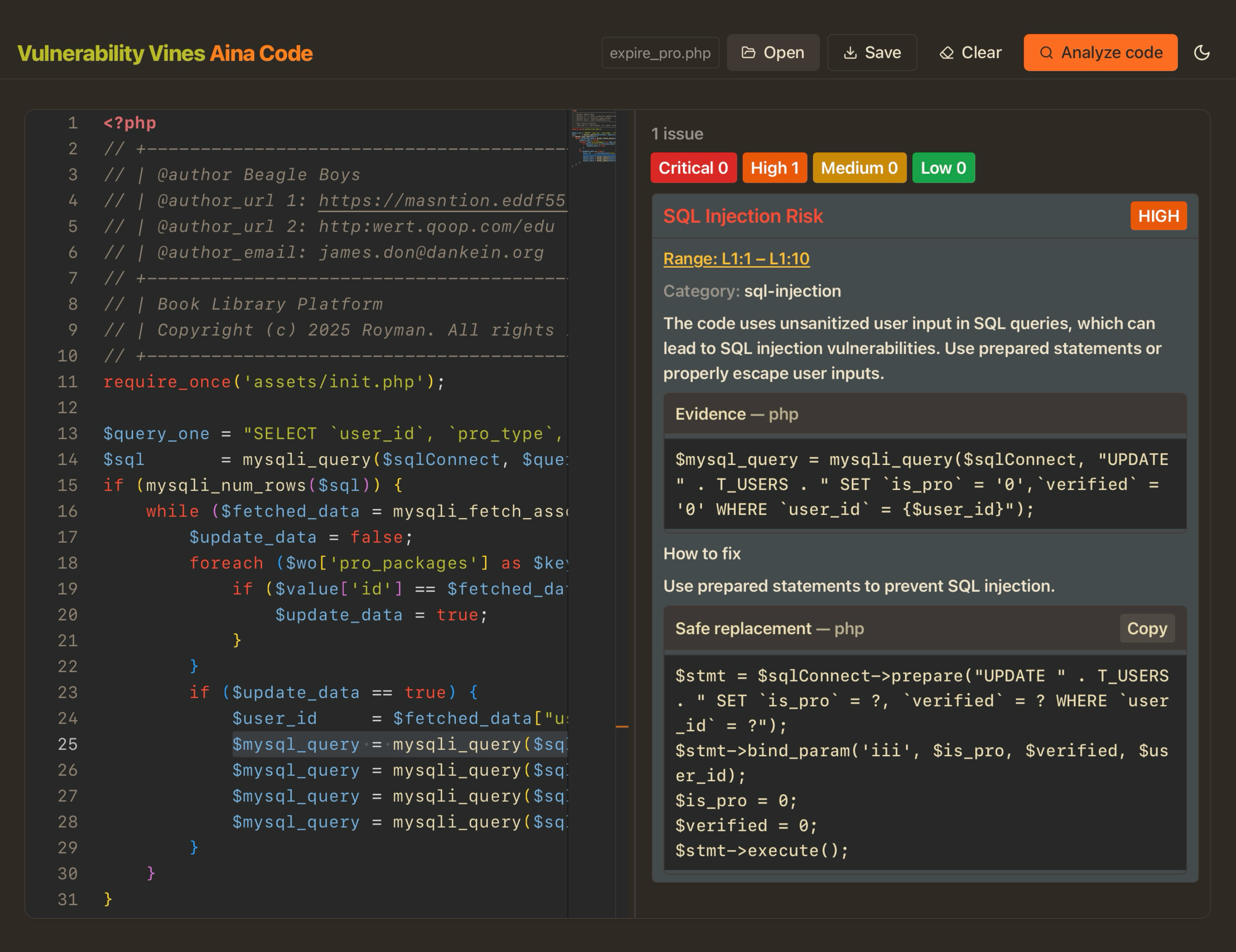
Detect Vulnerabilities in Source Code, with Lightning-Fast SAST.
AinaCode analyzes every commit for insecure patterns, secrets, and misconfigurations—AI-assisted rules catch what linters miss and turn results into clear, fix-ready guidance.

Vines AI + RCCE — Full NIST SP 800-53 Audit & Compliance
RCCE professionals use Vulnerability Vines AI to secure your organization end-to-end. Across all 22 domains they examine each checklist line, interview and test, collect evidence, recommend fixes, implement, and verify— delivering an evidence pack + POA&M with owners and deadlines.

- 🧭 Baseline selection (SP 800-53B) & tailoring
- 📑 SSP narratives, diagrams & control inheritance
- 🔎 53A methods: Examine / Interview / Test with evidence
- 🧪 DevSecOps: SAST/DAST/SCA, secrets, SBOM & signed artifacts
- ☁️ Cloud & K8s controls: CSPM, IAM least-priv, admission & runtime
- 🔐 Zero-Trust, PAM/JIT, MFA/SSO across identities & endpoints
- 📡 SIEM/XDR detections, logs, BCP/DR with immutable backups
- 🤝 Privacy & TPRM: RoPA/DPIA, vendor clauses, continuous posture
